Raid arrays on Debian

The Tests
I ran 3 tests, each test with and without load.

Conclusion
Even though the raid 5 has higher reads without load in some cases, Raid 10 seems to have better writes and better overall performance during load.

The Tests
I ran 3 tests, each test with and without load.

Conclusion
Even though the raid 5 has higher reads without load in some cases, Raid 10 seems to have better writes and better overall performance during load.
I have Telus Optik TV with a PVR and a few other TV cable units. I also have a separate Telus Internet connection to my house. These two services are separate. Why? My Internet connection is a business connection which could not be bundled at the time with Optik TV. So I had to have two separate pipes activated in order to receive both services.
Here’s the problem. Optik TV requires an internet connection in order for some of the subtle Optik services to work properly. For example: The streaming music channels require internet access in order for the preview and album artwork to show properly on the screen. Also Optik apps such as Netflix and the weather network app require internet in order to stream movies or get weather information downloaded. None of the features worked because there was no internet access. My home computer network worked fine as it was on a physically separate ADSL connection.
How-to enable Optik TV with internet when internet is not bundled with the TV service.
The first trick is disable the Actiontec router’s firewall(nat) and configure the box for “bridged mode”. This isn’t easy since the menu option is hidden. You can enable this option by hacking the advanced configuration page while logged into the Actiontec modem.
Step 1: Login to your Actiontec router and go to the advanced setup page.
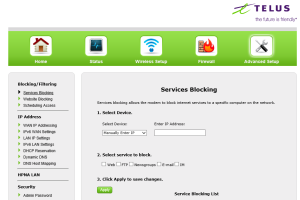
Step 2: Click on Wan IP Addressing. You’ll see an option to select an ISP protocol. The default might be RFC 1483 by DHCP. This is what normally works for Optik TV and internet, but this hides your TV units and internet access is blocked since I don’t have a valid connection via this network. The goal now is find the hidden radio button that allows the unit to be put into bridged mode.
Press F12 to activate your browsers developer mode and look for “rfc_1483_transparent_bridging” line. Change the value from display value from none to block.
You’ll now suddenly see a radio button option to enable transparent bridging. Select the radio button and apply the settings.
Step 3: Plug one of the LAN Ethernet connections on the Actiontec router into your own home network connection and reboot all your TV devices.
Done!
You will see that your TV units and PVR will still receive the TV channel feed from Optik, but your devices will receive an IP address from your home local network and they will have proper access to the internet.
References: http://npopson.com/archives/2202
I learned a neat antispam technique from a good colleague of mine on how to help stop spam email coming into your mail host. The goal is to trick spamming mail servers to hit a fake mail server, thus causing them to give up and not attempt a 2nd connection to your true mail server. The technique to accomplish this is to configure your MX records in DNS and rank your “true” mail server lower than your fake one. ![]()
Here’s my example below using bind in Linux.
root@estone:~# host estone.ca
estone.ca has address 206.116.5.55
estone.ca mail is handled by 10 mail1.estone.ca.
estone.ca mail is handled by 20 mail.estone.ca.
root@estone:~#
Now hopefully when a spam engine mail server attempts to connect to my fake mail1 email server, it will of course fail(because their is no mail service on the mail1 host) and then hopefully give up.